The internet is one of the most impactful technologies of today, enabling billions of people to communicate with family members around the globe, to share photos with one another, and to collaboratively edit documents in real time. Most of these systems are built on cloud architectures where centralized servers store user information and synchronize that data across user devices. The image below illustrates how this architecture typically works. When a user makes an edit on their laptop, the update is sent to a trusted third party server which synchronizes the data and forwards it to another user's cell phone.
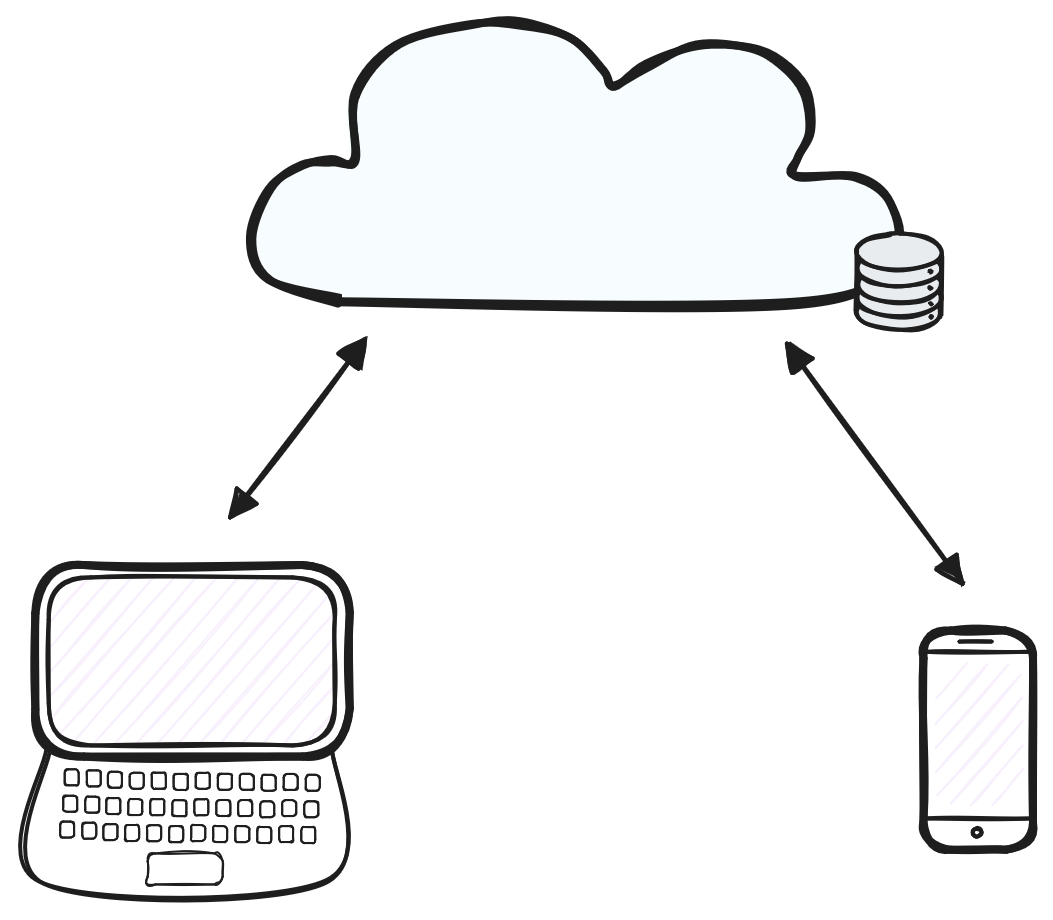
A traditional cloud architecture.